Risk and vulnerability analyses 2025
Last published: 11 September 2025
Financial institutions’ use of information and communications technology (ICT).
In short
|
|
Cyberthreat levels are high and affected by geopolitical changes |
|---|---|
|
|
Norway’s financial infrastructure is robust, secure and efficient |
|
|
Effective emergency preparedness is crucial for managing serious incidents |
|
|
Total losses resulting from fraud continue to increase |
|
|
The most important vulnerabilities in the financial sector are related to institutions' defences against cybercrime, the governance model for ICT operations and inadequate vendor management |
1. Summary
Finanstilsynet’s assessment is that Norway’s financial infrastructure is robust, secure and efficient. While there is a high level of preparedness, it needs to be continuously developed in line with changes in the threat landscape. Financial services also require stability in other infrastructure such as power supply and electronic communication. Digital robustness and resilience in the financial sector are crucial for maintaining trust in the financial system. Serious failures in ICT systems can threaten financial stability and affect civil protection, regardless of whether the failure is caused by criminals or state actors or by operational disruptions.
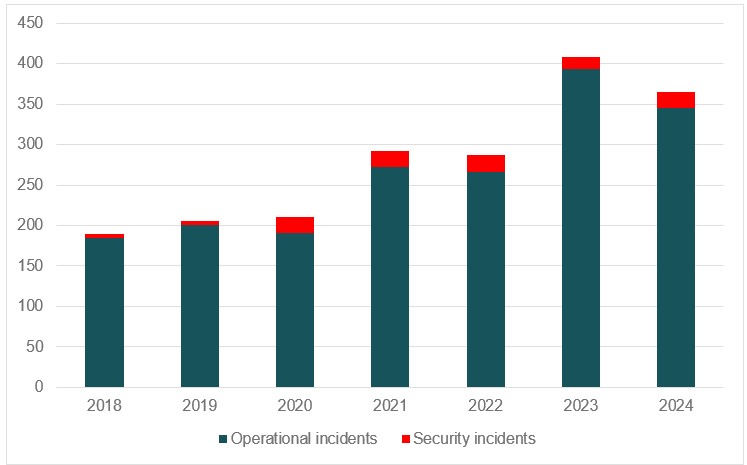
In 2024, there were no ICT incidents with implications for financial stability, and fewer serious incidents than in 2023 were reported. At the same time, there were some incidents that could have led to significant disruptions if they had not been resolved quickly. Some incidents received a lot of media attention, including incidents that led to errors in customers' account balances. The institutions' operational stability and the availability of payment services and other customer services remain consistent with the past three years and are considered to be satisfactory.
The cyberthreat level is high and constantly changing. The threat landscape and geopolitical changes make institutions’ security and emergency preparedness work both more important and more challenging than before. This means that new and more stringent measures need to be implemented to take account of scenarios that seemed unthinkable just a few years ago. Criminal actors are developing new methods, interacting in new ways and using new technology. States such as Russia, China, North Korea and Iran also represent a cyberthreat with significant capabilities. The changing geopolitical landscape raises questions about concentration risk and dependencies on a small number of service providers from the same region, both for the individual institution and for the financial sector as a whole.
Each institution within the financial sector bears an independent responsibility for safeguarding its own systems against intentional and unintentional incidents. This obligation applies even if some or all of the institution's ICT operations are outsourced.
Effective emergency preparedness in the individual institution and in the financial sector as a whole is crucial for the ability to handle serious incidents to minimise the consequences for users, the financial system and society at large. Robust and well-structured contingency solutions and processes are a prerequisite for this and must be continuously developed. These endeavours must be undertaken both internally by the institutions themselves, in cooperation with their service providers and through collaborative initiatives within the industry and with the authorities.
Supervisory activities in 2024 uncovered weaknesses and vulnerabilities in the institutions' follow-up of ICT activities. Complex supply chains, with multiple service providers and subcontractors in the value chain, increase the risk of supply chain attacks and operational incidents. At several inspections, Finanstilsynet highlighted shortcomings in vendor management, including cases where ICT activities are outsourced to subsidiaries or alliances, inadequate procedures for managing and controlling service providers’ accesses and inadequate follow-up of incidents at service providers. Furthermore, it was revealed that a number of institutions had not carried out business impact analyses and therefore failed to include business priorities and assessments of risk tolerance in their contingency plans. At many inspections, inadequate internal reporting related to ICT activities and ICT risks was also pointed out, as well as deficiencies in the institutions' change management.
Institutions and service providers have highlighted several key risks and vulnerabilities related to ICT operations to Finanstilsynet. Attention is drawn to the risks associated with fraud, particularly through social engineering and ID theft, and the danger of cyberattacks and other malicious attacks. There has been heightened awareness of the risks associated with geopolitical changes. The institutions also highlight risks associated with the need for changes as a result of new regulations and longer and more complex supply chains.
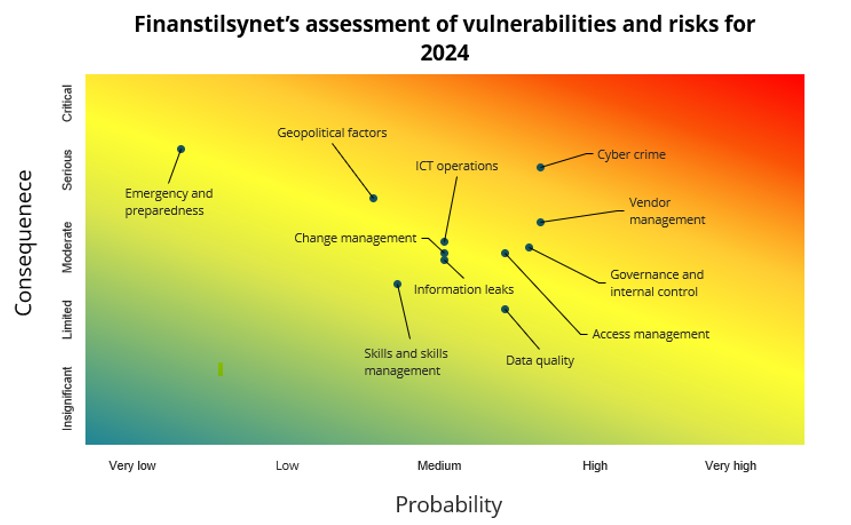
Finanstilsynet regards vulnerabilities related to institutions' defences against cybercrime as the most significant risk associated with their use of ICT, where the overall risk is still deemed to be high and somewhat increasing compared with 2023. Vulnerabilities related to access management, governance model, internal control and vendor management also represent key risks. High dependency on key service providers outside Europe also requires increased attention from institutions and supervisory authorities.
Losses resulting from fraud continue to increase and totalled NOK 1,227 million in 2024, an increase of 32 per cent from 2023. Parallel to this, institutions are preventing an increasing number of fraudulent transactions through their systems and controls. The increase in fraudulent activity indicates that institutions must continue to put considerable effort into anti-fraud initiatives.
The new regulation on ICT security, the Regulation on Digital Operational Resilience in the Financial Sector (DORA), is expected to enter into force in 2025. The primary objective of DORA is to enhance operational resilience and promote robustness, financial stability and customer protection, and to safeguard vital functions in society. DORA is based on the same principles as the current regulations but entails more extensive and stricter requirements. Furthermore, DORA imposes a number of requirements to be met by institutions’ board of directors and management relating to the establishment of a framework for governance of ICT activities, including ICT risk.
In 2025, Finanstilsynet will supervise important areas such as the institutions' efforts to strengthen their defences against cyberattacks and prevent adverse incidents, preparedness for handling serious situations, the use and follow-up of service providers, as well as management's governance of ICT activities and ICT risk.
2. The threat landscape
2.1 Geopolitical changes
The current changes in the geopolitical landscape mean that institutions, but also the authorities, need to assess how this affects the threat landscape, whether it gives rise to new or changed risks, and whether measures are needed. Institutions must assess how the changes affect their operations. Among other things, they must assess concentration risk and dependencies on a small number of service providers from the same region and consider their risk exposure related to the use of cloud services and the risk posed by a lack of European alternatives. This may necessitate an assessment of potential risk-mitigating adjustments, for example the re-establishment of OnPrem solutions1), which will entail increased costs for the institutions. The changes may also create uncertainty for institutions regarding data retention, including whether data can be transferred to countries outside the EEA. This includes personal data.
2.2 The cyberthreat landscape
The threat to the financial sector remains high and receives a great deal of attention in the industry. Threat actors are constantly adapting to institutions' defensive measures, seeking to exploit new vulnerabilities in the value chain and adopting new technology. At the same time, increased digitalisation gives threat actors a larger attack surface. Exploitable security holes can result in information leaks and/or unauthorised changes to an institution’s systems and infrastructure.
The threat to critical infrastructure, including the financial system, has increased due to changing geopolitical tensions. Institutions must assess how the changed threat landscape affects their operations and provision of services, what consequences this will have for ICT risk, and whether there is a need for measures.
The Norwegian National Security Authority (NSM), the Norwegian Intelligence Service (NIS) and the Norwegian Police Security Service (PST) all highlight a significant threat from state actors. PST expects Norwegian institutions to be affected by cyberattacks from countries such as Russia, China, North Korea and Iran. NSM also points out that the security policy situation indicates that new and more stringent measures need to be implemented to take account of scenarios that seemed unthinkable just a few years ago. This supports Finanstilsynet's comments to the institutions that worst-case scenarios must form the basis for contingency testing.
In its annual threat assessment for the financial sector, Nordic Financial CERT (NFCERT) points out that the overall cyberthreat against the financial industry has stabilised at a high level. The geopolitical landscape is identified as the most likely driver of significant changes in the threat landscape. As in 2024, organised criminal groups represent the most likely threat. NFCERT also points out that state actors are likely to collaborate with organised criminals, which can make it challenging to identify whether the attacker is a state actor or an organised criminal.
Complex supply chains, with multiple service providers and subcontractors in the value chain, make institutions vulnerable to supply chain attacks and operational incidents at several levels. In the summer of 2024, a faulty software update at the company Crowdstrike affected several sectors globally. Although the incident had relatively little impact on Norwegian institutions, it highlighted the vulnerability of long, complex supply chains. At the same time, there is a high concentration in the use of certain service providers to the Norwegian financial industry, which means that the consequences of incidents affecting the financial system can be amplified.
In 2024, incidents were reported where employees were asked about the institution's ICT systems, for example through LinkedIn, and were subject to spear phishing attempts. As the institutions' digital defences against cybercrime are continuously being strengthened, threat actors will increasingly try to gain access by building relationships with individual employees. The insider threat in the financial industry is considered to be constant, and insiders with financial motives of their own pose the most likely threat. The police's Threat Assessment 2025 points out that employees in banking and finance will be particularly vulnerable to bribes, pressure or threats from criminal actors who are willing and able to exploit people in key positions to carry out criminal acts. As banks have improved their cyber security, they are considered to be particularly attractive targets, and the use of insiders obscures the criminals' links to the criminal act. According to the Threat Assessment, several bank employees in Norway are under investigation, suspected of granting loans on false grounds, leaking sensitive customer data and misusing access to the banks' systems.
|
Security incidents in institutions' or service providers' ICT systems can have serious consequences for affected institutions. As security mechanisms at institutions or service providers are improved, threat actors may increasingly use insiders as a pathway into the ICT systems. Despite a high level of awareness and strengthened defences in the institutions, Finanstilsynet believes that technological and geopolitical developments require that preventive efforts are kept high on the agenda. The threat to the financial value chains is significant and can have a broad impact. Due to the high concentration in the use of certain service providers, Finanstilsynet assesses that incidents at the institutions' service providers can have serious consequences for the financial infrastructure. |
2.3 Measures implemented by the institutions to strengthen digital resilience
Each institution within the financial sector bears an independent responsibility for safeguarding its own systems against intentional and unintentional incidents. This obligation applies even if some or all of the institution's ICT operations are outsourced.
Responsibilities of the board of directors and management
Financial institutions' board of directors and management (management body) are responsible for addressing the ever-increasing ICT threats facing the sector. Management must continuously seek to have updated knowledge of the ICT risk landscape in order to be able to properly inform and advise the board of directors. It is also crucial for the institution to be proactive in implementing robust cybersecurity measures to strengthen defences against potential attacks and establish good contingency plans to mitigate the consequences of incidents.
The Digital Operational Resilience Act (DORA) aims to strengthen the resilience and robustness of institutions in the financial sector and is expected to enter into force in 2025. DORA imposes a number of requirements to be met by institutions’ management body relating to the establishment of a framework for governance of ICT activities and management of ICT risk. Among other things, they must at all times have sufficient knowledge to be able to understand and assess the institution's ICT risk and its impact on operations.
Understanding the risk landscape
The management body must ensure that the institution at all times has up-to-date knowledge and an understanding of the ICT risk landscape. This means that the institution must establish processes for the continuous gathering of information on relevant threats and vulnerabilities that may affect its ICT operations, also when the activities are outsourced. It also includes keeping abreast of developments in cyberattacks, malware, phishing methods and the use of new technology. The institution must also be familiar with regulatory requirements and industry standards that apply to cyber security and data protection in the financial sector. Collaboration with security organisations and other financial institutions can provide useful insight into measures to improve defences against ICT threats and make the financial institution better prepared for potential threats.
Measures to strengthen defences against ICT threats
In order to strengthen their defences against current ICT risks, financial institutions should implement both technological and organisational measures. The security solutions must ensure continuous monitoring of the ICT infrastructure and protect it against cyberattacks. Firewalls, authentication solutions, intrusion detection systems and antivirus software need to be regularly updated to deal with new threats. Production systems must be updated with new, controlled and approved versions and security patches. An important proactive measure is to establish strict access controls and authentication mechanisms to ensure that only authorised personnel have access to sensitive data and systems.
Increased training and higher awareness among employees of security procedures and threats such as phishing and social engineering are crucial to reducing the risk of human error. In addition, the institution must ensure that contingency plans based on business impact analyses (BIA) are developed and tested to ensure rapid response and recovery in the event of a security breach. Having updated knowledge of the ICT threat landscape and following best practice for cyber security will reduce the likelihood of malicious cyberattacks having serious consequences for the institution.
2.4 Collaboration on threats and security improves risk understanding
Collaboration in the area of security on different arenas provides better risk understanding. Such collaboration is important to strengthen defences against cybercrime both for the individual institution and for society at large, whether through cooperation between authorities nationally and internationally, between authorities and institutions or between institutions. Collaboration with service providers is also important.
DORA includes provisions for collaboration and information sharing between institutions to increase awareness of cyberthreats and help improve institutions' digital operational resilience. The cooperation Nordic financial institutions have established through Nordic Financial CERT (NFCERT) is in accordance with the provisions of DORA. The cooperation has contributed to raising institutions' awareness of the current threat and risk landscape and strengthened their efforts to improve their resilience against cyberattacks and their ability to respond quickly and effectively to cyber security threats and cybercrime. The threat reports that are prepared are useful tools for the institutions' security work.
Institutions that choose not to participate in collaborative efforts could be less prepared to deal with digital threats and adverse incidents.
DORA also contains provisions for cross-sectoral cooperation between authorities and between countries. The European Financial Supervisory Authorities have established a framework for coordination between countries in the event of systemic cyber incidents (EU-SCICF). The purpose is to facilitate rapid communication and coordination between supervisory authorities and other relevant bodies to prevent systemic failure in the event of a serious incident. The EU-SCICF is operational for crisis mode, and work is underway to further develop the framework to include collaboration on the understanding of cyber risk, trends and the evolving threat landscape, as well as on exercises. The EU-SCICF's first exercise was conducted in April 2025. Finanstilsynet is Norway's point of contact.
Finanstilsynet and Norges Bank also participate in the European Systemic Risk Board's (ESRB)2) working group (ESCG) tasked with mapping systemic cyber risk and how a cyber incident could trigger a systemic crisis.
During 2024, Norges Bank and Finanstilsynet developed a framework and a process for assessing systemic ICT risk and how systemic ICT incidents can jeopardise financial stability. Representatives from the industry were also involved in this process. In this endeavour, recommendations and definitions from the ESRB and others have been included in the assessments. In 2025, the framework will be used in a pilot project where a small number of scenarios will be assessed.
In 2021, Norges Bank and Finanstilsynet established a framework for threat-led penetration testing of cybersecurity in the financial sector (TIBER-NO)3) and in this context also the TIBER-NO forum4). This framework provides guidelines for testing financial institutions' ability to detect, protect against and respond to advanced cyberattacks and shall help increase resilience against such attacks. Four institutions have carried out testing according to TIBER-NO. The tests indicated that their security level appeared to be satisfactory. The TIBER-NO forum is a useful collaboration arena for such testing and work on ICT security for participating institutions. The testing helps raise the quality of security work and provides realistic exercises to strengthen emergency preparedness. DORA introduces a requirement for threat-led penetration testing (TLPT) for institutions' critical or important functions and sets a number of requirements for conducting the tests. The TIBER framework can be used for TLPT testing under DORA.
Both Finanstilsynet and several institutions in the financial sector are partners in the Norwegian National Cyber Security Centre (NCSC), which is an arena for national and international cooperation on identification (detection), management, analysis and advice related to cyber security. The NCSC has been established by the Norwegian National Security Authority (NSM) to enhance Norway's resilience and preparedness in the digital domain. Participation gives the institutions and Finanstilsynet access to updated knowledge about the risk landscape in the cyber security domain, as well as the opportunity to interact with other stakeholders to handle cyberthreats and attacks.
To address cyber threats and help make institutions better prepared to comply with an increasingly complex and detailed regulatory framework in the ICT domain, Finance Norway has established a collaboration forum for ICT security. The aim is, among other things, to strengthen the institutions' security work, contribute to a holistic approach to security work and, where appropriate, collaborate on common challenges.
3. Emergency preparedness in the financial system
The Ministry of Finance has defined 'Ensuring society's ability to provide financial services'5) as one of three fundamental national functions (FNF) within its sector. A robust financial infrastructure is crucial for financial stability and well-functioning markets and a prerequisite for maintaining the basic functionality of society.
The Norwegian financial system is among the most digitalised in the world. Norwegian financial institutions have been at the forefront of developing efficient and customer-friendly services that capitalise on a generally high level of digital literacy in society. Digitalisation brings great benefits to financial institutions, customers and society but also new risks and vulnerabilities. In extreme cases, serious incidents and the disruption of fundamental financial services may pose a threat to financial stability and have implications for national security, whether the incident is caused by crimes committed to obtain a financial gain, by targeted attacks or by operational disruptions. Financial services also require stability in other infrastructure, such as power supply and electronic communication.
Effective emergency preparedness in the financial system increases the ability to prevent and manage serious incidents, thus mitigating the consequences for the financial system and its users. Robust contingency solutions and processes are a prerequisite for this work and must include all levels involved.
The individual institution's contingency solution constitutes the first line of defence in the financial infrastructure. The institutions must also have good operating procedures and contingency solutions and set clear requirements for and closely monitor the emergency preparedness of their service providers. In some cases, it may be necessary for actors to jointly establish contingency solutions, for example within shared services in the payment system.
There may also be a need for contingency solutions administered by public authorities, e.g. for infrastructure such as power supply and electronic communications, but also for financial infrastructure.
Several serious incidents have shown that good cooperation between actors is important. Reporting of incidents to Norges Bank and Finanstilsynet within their respective areas of responsibility provides a basis for assessing the seriousness of the incident and the possible need for follow-up by the authorities. Such reporting is thus part of the authorities' preparedness structure. NFCERT and Finanstilsynet collaborate on the role as sectoral response environment (SRE)6) to manage ICT security incidents in the financial sector. The Financial Infrastructure Crisis Preparedness Committee (BFI)7) was established in 2000 to help ensure good coordination in the event of serious incidents in the financial infrastructure. The committee conducts an annual emergency preparedness exercise. In 2024, an extraordinary meeting of the BFI was convened in connection with a serious incident, and the committee was operational within minutes. In addition, Finanstilsynet, Norges Bank and the Ministry of Finance have plans in place to deal with serious incidents and will interact when necessary. In the event of major incidents, national crisis management measures can be implemented.
In addition to the contingency measures undertaken by the industry and the authorities, the self- preparedness of consumers and enterprises8) is important. The Norwegian Directorate for Civil Protection (DSB) and Norges Bank have recommended that consumers should have access to several different payment cards, available cash in different denominations and access to accounts in more than one bank for different payment options if parts of the financial system become unavailable. Merchants should also be able to offer alternative payment solutions.
In the Official Norwegian Report 'Now it's serious' (NOU 2023:7)9), the Norwegian Total Preparedness Commission pointed out that it is important for the financial sector to plan for rare crisis scenarios, e.g. that the electronic infrastructure becomes unavailable for a long period, requiring a shift to alternative solutions. The report pointed out that the financial sector is working systematically on preparedness and risk management. This is supported by National Security Authority's annual threat assessment for 2022,10) which points out that there is much to learn from the financial sector's long experience of working with security and risk management. The International Monetary Fund's (IMF) review of the Norwegian financial system in 2019/2020 rated Norway's work on cyber risk as advanced.11)
3.1 Requirements for institutions' work on emergency preparedness
Institutions' contingency solutions constitute the first line of defence in the financial infrastructure. Their work on ICT security and good contingency plans and exercises is therefore important.
A key part of the institutions' contingency planning is to carry out business impact analyses (BIA). Such an analysis shall form the basis for the institution's contingency plans and implementation of measures and ensure that these are established based on business-critical priorities and in alignment with the institution’s risk tolerance. The institutions must also take into account their significance and role in society to ensure that the institution's emergency preparedness contributes to strengthening the overall resilience of society.
Institutions and their service providers must ensure that their operations, including ICT solutions, can be restored after cyberattacks and must have updated and tested plans for this purpose. Assessments and measures must be carried out to ensure that institutions' contingency solutions and backups of systems and information are protected against cyberattacks. In addition to plans for restoring systems and reproduce any lost data, the institutions must have plans for managing incidents until systems and lost data are restored. The institutions must also ensure that they have updated communication plans for various incident scenarios, as well as access to emergency power to safeguard ICT operations in the event of a power outage.
Emergency response exercises, including those based on realistic scenarios, are intended to help institutions train to handle an emergency situation. In addition, such exercises will be a good test of established contingency solutions. The tests must be designed to assess the suitability of the contingency solutions and the robustness of the organisation and contribute to strengthening the institution's preparedness. To ensure that internal instructions and plans function well, also in scenarios where ICT services are unavailable for an extended period, the testing of both the institution's own and outsourced ICT services must include relevant worst-case scenarios. Recovery plans for how quickly the institution's own systems can be reestablished and alternative operations be initiated, as well as assessments of the consequences any downtime may have for the institution and its customers, must be included in the testing. Results from the tests must also be reviewed to eliminate weaknesses and deficiencies in contingency systems and procedures.
The institutions must have procedures in place to ensure that the need to adjust contingency solutions and the emergency response organisation is assessed when implementing changes.
The new regulation on digital operational resilience in the financial sector (DORA) entails extensive requirements for institutions' contingency planning, including requirements for backups, incident response, recovery and testing of digital operational resilience.
3.2 Work on preparedness in the payment system
Security and effective emergency preparedness are prerequisites for an efficient payment system. In addition to the institutions' contingency planning related to customer payment services, emergency preparedness within the payment system has also been assessed by both the Payments Committee and a working group appointed by the Ministry of Finance.
According to the Payments Committee's report 'Safe and simple payments for everyone' (NOU 2024:21)12), preparedness in the payment system is generally good, but there is room for improvement. The committee therefore proposed a number of measures to ensure adequate emergency preparedness, such as expanding BankAxept's extended backup solution, expanding STIP13) solutions, establishing contingency solutions for consumer payments and separate regulations for use in contingency situations.
While it may be both appropriate and practical for actors to find good contingency solutions themselves, the authorities may not consider these sufficient from a societal perspective, and additional measures may be necessary. A regulatory framework for use in serious emergency situations therefore seems appropriate. The framework should be service and technology neutral in order to reflect market developments and the importance of individual players and must include requirements for regular testing and regulation of responsibilities and risks associated with various emergency situations.
A working group appointed by the Ministry of Finance in 2023 has assessed the emergency preparedness of the digital payment system, including how well it is adapted to very severe crisis scenarios and the increased threat level.14) The working group was tasked with:
- mapping the payment system and identifying scenarios that could affect the ability to make payments and to access account information.
- analysing and identifying possible measures and preparing a specific plan and possibly an in-depth impact study.
The working group has assessed 51 measures that may mitigate the consequences of the identified scenarios. The working group recommends implementing 18 of these measures aimed at strengthening the ability to make card payments and carry out account payments, clearing and settlement under various scenarios. The purpose of several of the measures is to strengthen existing backup solutions or establish new ones. Some measures are aimed at particularly important components of the digital payment system, while other measures are recommendations for households and merchants. The measures affect all actors in the payment system and to some extent their service providers.
The working group identifies four of the 18 measures as particularly important for making the digital payment system more robust in the face of very severe scenarios:
- daily reporting of customer data from the banks to an independent data warehouse
- establishment of independent emergency preparedness procedures for the banks' critical services
- improvement of STIP services for BankAxept
- expansion of BankAxept's extended backup solution from one to four weeks
Finanstilsynet supports the working group's recommendations and believes that the proposed measures will help strengthen emergency preparedness in the payment system.
3.3 Institutions' contingency planning
Contingency planning to minimise the consequences of incidents, but also to address emerging threats (or risks), is generally given high priority by institutions and their service providers. The institutions' efforts to prepare for the new ICT security regulations, DORA, have contributed to this. These endeavours are undertaken both internally by the institutions themselves, in cooperation with their service providers and through collaborative initiatives within the industry and with the authorities.
Through its supervisory activities, Finanstilsynet gains insight into the institutions' contingency planning and testing activities, including testing organised by service providers. Finanstilsynet observes that the institutions have increased awareness of, and progress in, conducting business impact analyses (BIA), and that these are being used in their contingency planning. Finanstilsynet also notes that the institutions are increasingly using realistic scenarios, such as intentional cyberattacks and worst-case scenarios, as a basis for contingency testing.
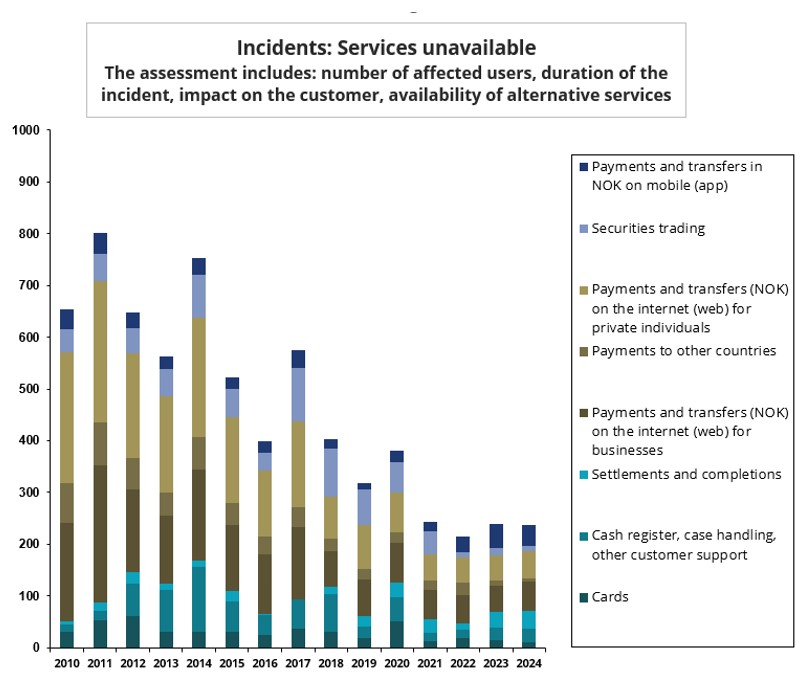
Incidents reported in recent years show that organisations and their service providers are resolving problems in their ICT solutions faster than before. This, combined with measures to improve operational stability, has over time improved the availability of payment services and other customer services, see section 7.7. Improved knowledge of ICT solutions, measures implemented in the wake of previous incidents and better preparedness to handle incidents are factors that have contributed to this.
In recent years, BankAxept's backup solution has been further developed and its duration extended from up to six hours to up to seven days for critical players within retail trade with wide distribution networks, such as grocery chains, pharmacy chains and fuel outlets. The rollout of BankAxept's payment cards with offline PIN support, which started in 2023, has also helped improve preparedness.
Finanstilsynet and BFI have paid a great deal of attention to risks and challenges in the financial infrastructure due to the Covid-19 pandemic, the war in Ukraine, the conflict in the Middle East and the recent conflict between India and Pakistan. Contact with the institutions and experience from extraordinary BFI meetings show that the key institutions in the Norwegian financial infrastructure have well-organised contingency structures and contingency plans that can be quickly activated. In addition, the institutions demonstrate a strong ability to implement measures in line with changes in the threat landscape.
Although the institutions' contingency planning and related efforts appear to be solid, they must be continuously developed in line with changes in the threat landscape and increasing demands for operational resilience. Supervisory activity shows that the institutions have room for improvement in several areas. Among other things, their contingency plans must be based on completed BIAs, they must be more actively involved in service providers' testing, and realistic worst-case scenarios must be included in the testing.
4. Finanstilsynet’s observations
4.1 Supervision of ICT and payment services in 2024
Information from completed inspections
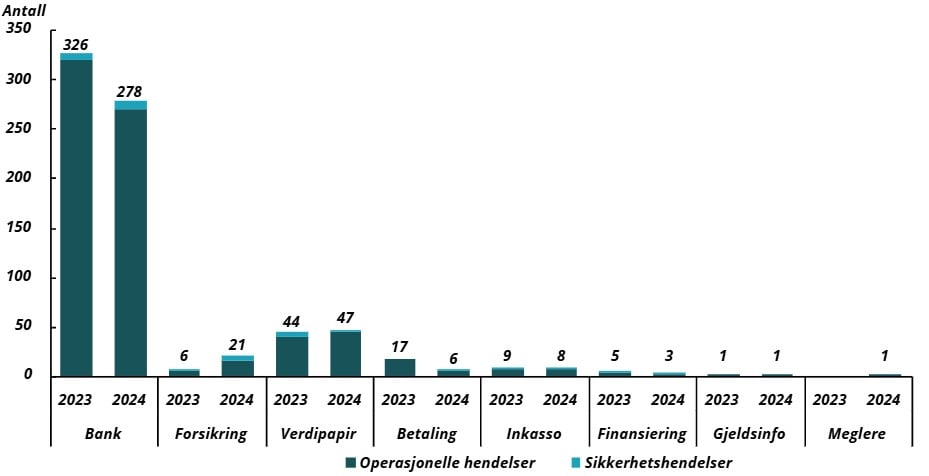
In 2024, 17 inspections focusing on ICT and payment services were conducted at eight banks, two insurers, two fund management companies, two electronic money institutions, one real estate agency, one debt collection agency and one market operator.
Reports from the inspections have been published on Finanstilsynet's website. Finanstilsynet would like to highlight the following topics:
ICT operations
Incident management
At several inspections, Finanstilsynet questioned the institution's follow-up of service providers' incident reporting in terms of identifying root causes and measures. Finanstilsynet also noted the institutions' failure to follow up whether service providers implement measures and take sufficiently steps to reduce the risk of recurrence. In its inspection reports, Finanstilsynet expresses an expectation that the institutions will have adequate incident management procedures regardless of whether the service is outsourced.
Change management
During several inspections, deficiencies were identified in the institutions' change management process. Several of the institutions had not included less complex and standardised changes, such as DevOps15) and automated changes16), in its established change management process. Finanstilsynet emphasised that an established process must include all types of changes. The institution must also assess which control requirements are necessary when implementing less complex changes that are assumed to involve low risk. Such changes should be monitored to assess whether they cause an increase in incidents.
Several institutions have not included a requirement in their change management process to assess the need to adjust their contingency plans. Finanstilsynet pointed out that change management processes should include an assessment of whether the change requires an update of current contingency plans to ensure that the contingency plans reflect the institution's operating environment and risk landscape.
|
Finanstilsynet expects that all types of changes are taken into account in the institution's change management processes, and that the processes include an assessment of the need to update contingency plans. |
Outsourcing of ICT activities
Due to supervised institutions' extensive outsourcing of ICT activities, Finanstilsynet will continue to focus on the institutions' management and control of service providers, partly in consequence of heightened concentration risk and geopolitical changes. Again in 2024, Finanstilsynet found shortcomings in the institutions' follow-up of outsourced activities during inspections. Finanstilsynet would like to highlight the following topics:
Vendor management
Several deficiencies related to institutions' accountability for outsourced operations were identified at inspections in 2024, including the need for institutions to impose requirements on service providers and ensure adequate reporting demonstrating compliance with these requirements. This must be included in the institution's procedures for outsourcing ICT activities. In addition, Finanstilsynet underlined the importance of carrying out second and third line controls to ensure compliance with the institution's requirements and ensuring that the institution has sufficient resources and ICT expertise to carry out the controls.
In cases where ICT activities are outsourced to a subsidiary or an alliance, several inspections revealed inadequate requirements concerning the service provider's role and responsibilities. The quality of the institutions' follow-up of such outsourcing was observed to vary, largely reflecting the size of the institution.
Finanstilsynet recognised that subsidiaries and alliance partners contribute to competence sharing and streamlining across group entities but pointed out that the individual entities are not sufficiently involved in the preparation of common strategies and procedures and in adapting these to their own operations. At several inspections, Finanstilsynet observed inadequate governance by the institution, for example a lack of board involvement and failure to operationalise strategies.
Finanstilsynet also pointed out at some inspections that the ICT Regulations’ provisions apply irrespective of whether the outsourcing is intragroup or external. The institutions must therefore ensure adequate follow-up of intragroup outsourcing. When it comes to shared services from alliance partners, Finanstilsynet emphasised that governing documents are expected to be adapted to the entity's operations and priorities, and that sufficient control is expected to be exercised to ensure compliance.
Management and control of service providers' accesses
Finanstilsynet has observed some improvement in this area, especially as a result of the institutions' measures based on lessons learned from adverse incidents. At some inspections conducted in 2024, Finanstilsynet nonetheless pointed to inadequate procedures for managing and controlling service providers' accesses, which increases the risk that employees at ICT service providers will misuse their access for non-work-related searches. Furthermore, several institutions lacked procedures for monitoring accesses assigned to service providers to uncover potential misuse. Finanstilsynet also pointed out that the institutions must ensure that ICT service providers establish solutions for access management as well as control procedures that, as far as possible, ensure that accesses are assigned and controlled for each individual assignment.
In its inspection reports, Finanstilsynet emphasised institutions' responsibility for managing and controlling service providers' access rights and pointed out that service providers' reporting must provide sufficient insight into accesses and access levels.
|
Independent assurance engagements Independent assurance engagements, such as ISAE3402 and ISAE3000 reports, can be a useful supplement to institutions' management and control of service providers. However, inspections have identified a trend whereby institutions process and utilise the content of the reports to a limited extent. Many of the institutions rely heavily, and at times uncritically, on the statutory auditor's review of the financial audit and give little consideration to whether it adequately covers their own service procurement. Finanstilsynet emphasises that such reports can be designed for a wide range of recipients, and that the institution must assess its scope and test objects against its own needs. In order to benefit from such reports, they must be incorporated into the institution's vendor management procedures. Institutions should carry out their own assessments and controls to ensure that the content of the reports is relevant and applicable to the institution. Furthermore, a process should be established to respond to any identified deviations or observations. In order to ensure good management and control of its ICT activities, including the ones that are outsourced, the institution should also carry out its own assessments and controls. |
Emergency preparedness
During inspections in 2024, Finanstilsynet highlighted several shortcomings within emergency preparedness. A number of institutions had not conducted contingency tests based on realistic scenarios, such as intentional cyberattacks. Many institutions had not carried out business impact analyses and therefore lacked business priorities and risk tolerance assessments in their contingency plans. Finanstilsynet observes that several institutions have increased awareness of, and progress in, developing a BIA, but has underlined the importance of this work being based on priorities set by their business units.
|
Business impact analysis as a basis for contingency planning A key part of the institutions' contingency planning is to carry out business impact analyses (BIA). The analysis will help ensure that the institution's contingency plans are prepared on the basis of business criticality. The institution's exposure to severe business disruptions and potential consequences (including breaches of confidentiality, integrity and availability) shall be assessed. The institutions' contingency plans shall support the requirements set out in their BIA and be based on the institution's priorities for restoring business-critical services and processes. Finanstilsynet expects institutions to design tests of their contingency plans that enable them to assess the suitability of the crisis solution and the robustness of the organisation. This means that the testing, both of the institution's own and of outsourced ICT services, must include relevant information security scenarios with worst-case scenarios where plans for recovery |
Reporting of ICT risk and compliance with governing documents
At several inspections, Finanstilsynet observed that there was no reporting on compliance with requirements set by the board of directors. To ensure that the requirements set out in governing documents are operationalised, this must be included in the regular reporting to the board. Furthermore, Finanstilsynet expects the institutions to carry out controls in the second and third lines of defence of requirements subject to reporting.
At many inspections, Finanstilsynet pointed out that the reporting of ICT risk was inadequate or was not included in the regular reporting to the board from the institution's independent control functions in the second line of defence. In several inspection reports, it was pointed out that the institution's reporting primarily focuses on information security and cyber risk and to a limited extent on more operational risks and vulnerabilities related to ICT operations. Deficiencies in reporting to management from the first line of defence were also identified, reflecting a lack of defined reporting requirements or insufficient operationalisation of requirements.
Finanstilsynet also raised concerns regarding whether the frequency and scope of the reporting are sufficient for the board to maintain effective oversight and governance of the institution's ICT risk. In Finanstilsynet's opinion, in order for the board to maintain oversight of the institution's operational risk, including ICT risk and ICT security risk, the second line of defence should regularly give the board a comprehensive and complete assessment and analysis of the institution's ICT security risk and vulnerabilities.
4.2 Institutions' assessment of critical aspects related to ICT operations
In discussions with Finanstilsynet, institutions and ICT service providers have highlighted several critical aspects related to ICT operations.
Governance
Several institutions indicate an increased understanding of the importance of a well-functioning governance model in the ICT domain, underlining that their work on DORA has helped them establish such a model. Furthermore, it is noted that institutions have demonstrated increased maturity in applying a risk-based approach to prioritise initiatives that are deemed critical to the institution. Small institutions find it challenging to ensure compliance with all regulatory requirements.
Skills and skills management
The institutions state that it has generally become easier to recruit ICT expertise, but that the recruitment of persons with specialist skills is more difficult and drives up salaries. The trend of reducing the use of consultants and building internal expertise is continuing and has a positive effect on recruitment. Institutions still highlight challenges in accessing and renewing expertise in older technologies.
The institutions report that it has become more challenging to describe the need for expertise in job adverts in the ICT domain. Among other requirements, upcoming European regulations stipulate the need for professionals with a holistic understanding of the regulatory framework.
Vendor management
The trend towards longer and more complex supply chains presents institutions with greater challenges in adequately managing their service providers. The institutions point out that many services from service providers are included in a number of customers' (institutions') services, which creates dependencies that are difficult for the individual institution to keep track of. This is illustrated, for example, by the fact that the implementation of changes by service providers frequently leads to errors that affect the entire industry.
Several institutions disclose weaknesses in their governance of outsourced ICT operations. The institutions highlight challenges related to the fact that service providers are not organised into three lines of defence in the same way as the institutions. This means that time is spent on clarifying responsibilities and finding the right expertise.
Geopolitical conditions
The institutions are keeping abreast of geopolitical changes and state that they are increasingly assessing concentration risk and their dependence on individual regions and countries. For example, the lack of European cloud service providers is emphasised. The increased uncertainty associated with the geopolitical situation has led to questions about whether the re-establishment of On-Prem solutions17) is necessary to ensure adequate control.
It is further reported that customs and currency-related matters may have financial implications in connection with the renewal of agreements with key stakeholders.
The institutions also monitor the vulnerability that critical submarine communication cables connecting to Europe may pose, including the fact that many service providers use the same cables.
Emergency preparedness and crisis management
The BIA will help ensure that the institution's contingency plans are prepared on the basis of business criticality. The institutions have devoted considerable effort to preparing such analyses to ensure that contingency plans and the work on information security can be based on the institution's priorities for restoring business-critical services and processes. Several institutions have carried out an extensive process to prepare an overview of its business areas and their important and critical functions.
4.3 Summary of the institutions' risk and vulnerability reporting
Finanstilsynet has collected risk and vulnerability assessments of ICT operations from payment service providers and other institutions, in accordance with the Regulations on Payment Services Systems, Section 2 third subsection, cf. the ICT Regulations, Section 3. For further details, please refer to Appendix 1.
Areas with the highest risk
In the reporting, the institutions were asked to state which conditions they perceive to constitute the highest risk. Fraud, especially through social engineering, was identified as the biggest risk area in the 2024 reporting. Another area that was highlighted by many, also in the 2023 reporting, was the risk of cyberattacks and other malicious attacks. This year's reports increasingly refer to geopolitical conditions.
A third area highlighted by many is regulatory risk. Particular reference is made to the new Digital Operational Resilience Act (DORA) and the third Payment Services Directive (PSD3) and the associated Payment Services Regulation (PSR). There is less reference to anti-money laundering legislation than before.
Risks related to the management of third-party ICT risk and the challenge of keeping track of long supply chains are also mentioned this year. Some institutions also highlight challenges in retaining ICT expertise and key personnel risk, particularly in connection with legacy systems and technical debt.
Governance
The reporting indicates that most institutions estimate the overall risk associated with governance as low in 2024, as was also the case in 2023. The trend is generally stable or decreasing.
More than 80 per cent of the institutions, up from just over 75 per cent the previous year, state that their ICT systems provide a good basis for managing and controlling operations, that the risk analysis process is well established and that they use recognised standards and guidelines in their ICT activities.
The institutions assess the risk of not maintaining oversight of business-critical ICT equipment and software, including licences, to be low, and believe that outsourcing agreements ensure the institutions' access and review rights. More than 80 per cent of the institutions assess that they possess strong procurement competence, including legal, technical and professional expertise. This is a clear increase from the previous year, when two-thirds reported the same. The institutions have responded that the risk associated with ongoing monitoring of service providers and deliveries is somewhat higher, with just over one in four assessing the risk as moderate or high.
More than 80 per cent of the institutions state that they comply with the principle of the three lines of defence in the ICT domain. An equal number confirm that they have policies in place that require ICT operations to be periodically reviewed by independent, qualified individuals, and that they carried out such a review during 2024. Nevertheless, just under 40 per cent report that the risk is moderate or high when it comes to maintaining oversight of the controls the institution relies on within the three lines of defence, broken down on controls that help ensure integrity, confidentiality and availability.
Within ICT security, over 80 per cent also consider the risk to be low when it comes to documented goals and security procedures. This is an increase compared with the previous year, when just over three quarters gave the same answer. More than two out of three institutions responding to this question believe there is moderate risk associated with missing or inadequate guidelines related to ICT security, including risk assessments of payment services and measures to protect users from identified risks. The trend is stable, which was also the case in 2023.
|
Finanstilsynet has noted that although the institutions believe they have good procurement competence, they nevertheless assess the risk associated with monitoring of service providers and deliveries as significant or high. Institutions in the Norwegian financial sector largely base their operations on deliveries from ICT service providers. Through its supervisory activities, Finanstilsynet often observes shortcomings in institutions' follow-up of outsourced ICT activities. Since adverse incidents are often caused by errors on the part of a service provider or subcontractor, Finanstilsynet emphasises the importance of effective follow-up of service providers and their deliveries. |
Data protection
More than two-thirds of the institutions assess the risk of compromising the integrity of the data they process in their systems as low. Roughly the same proportion of institutions also report that the risk associated with data protection is low.
The area where most institutions report moderate or high risk is logging of accesses to data and systems. A lack of control in this area can lead to failure to follow up unauthorised access or attempted access to data or systems. One institution reports high risk due to the lack of automatic notification of attempted unauthorised access.
Another institution reports high risk associated with agreements on data storage with service provider and documentation of data erasure upon termination of agreements. This is a consequence of inadequate follow-up procedures. However, the institution states that it is working on updating its procedures and increasing awareness and expertise in this area. More than 80 per cent of the other institutions assess the risk as low.
|
Finanstilsynet observes that the area where most institutions report moderate or high risk is logging of accesses to data and systems. Without adequate governance in this area, unauthorised access or attempted access can go undetected and unaddressed, increasing the vulnerability to security breaches and weakening the ability to follow up deviations. Another vulnerability related to inadequate logging is the risk of insiders who may be motivated either by direct financial gain or by giving outsiders access to data and systems. This underlines the need for clear procedures and effective access management mechanisms. |
Change management
Change management is an area where roughly half of the institutions consider the risk to be low. As in 2023, most institutions assess the risk associated with the complexity of ICT systems as significant, and more than half of the institutions assess the risk as either moderate or high. Institutions that assess the risk as high emphasise, among other things, that central systems are based on older and outdated technologies, that it is difficult to maintain control and expertise related to certain value chains, and that dependencies between systems, services and suppliers constitute a risk.
More than 80 per cent of the institutions consider the risk that new regulatory requirements will require changes to their systems as moderate or high. Institutions that assess the risk as high refer to a significant volume of new regulations, including DORA and anti-money laundering rules. They also point out that new regulations require updates to systems and procedures. Most institutions believe that new regulatory requirements entail increased risk for their operations.
|
Finanstilsynet has noted that about half of the institutions assess the risk associated with changes as low despite the fact that there were also many incidents in 2024 caused by errors in solutions following planned changes implemented by service providers, as described in section 7.4. Finanstilsynet believes that the errors should have been uncovered during the testing process and emphasises the importance of thorough testing by service providers and acceptance testing and internal controls on the part of the institutions. |
Operations
More than half of the institutions generally assess operational risk as low.
The institutions' oversight of outsourcing and associated risks is the area where the highest number of institutions assess the risk as high. As in 2023, approximately one-third of the institutions assess the risk associated with maintaining an up-to-date register of outsourced activities as moderate or high. The same assessment is made concerning whether there are sufficient resources and expertise in the second and third lines of defence, including whether deliveries are regularly monitored. Institutions that assess the risk as high refer to factors such
as a lack of resources or key person risk.
Approximately 40 per cent of the institutions report moderate or high risk related to operations due to technical debt. Institutions that have assessed the risk as high point to factors such changing priorities due to mergers, while others emphasise that key solutions are based on older and outdated technologies that need updating.
More than one of three institutions assess the risk that plans, processes and procedures for continuity and recovery of critical ICT systems and services are not regularly reviewed, as moderate or high. Institutions that assess the risk as high point out that procedures are inadequate and need to be adapted to the changing threat landscape.
|
In light of the ever-changing threat landscape, Finanstilsynet finds it concerning that more than one-third of the respondents assess the risk as moderate or high when it comes to continuity and re-establishment, and that procedures are inadequate and need to be adapted to the changing threat landscape. Finanstilsynet expects the institutions to give priority to managing the risk by implementing measures. |
Security
More than half of the institutions assess security risk as low. However, more than half of the institutions assess the risk associated with access to ICT security expertise as moderate or high, including the expertise needed to set requirements for service providers and monitor deliveries. One institution assesses the risk as high due to the fact that it is a small organisation, which results in high key person risk.
As in the 2023 report, about a third of the institutions assess the risk as moderate or high that the institution will not conduct regular security tests of its services. The institution that has assessed the risk as high points out that the frequency of security tests is too low. Some institutions also state that there is moderate or high risk linked to whether the institution has measures in place to protect itself against malicious attacks. However, only one institution responded that it assesses the risk as high.
|
As pointed out at inspections, Finanstilsynet considers security testing of services to be of vital importance. Finanstilsynet has noted that approximately one in three institutions assess the risk associated with the lack of regular security testing as moderate or high. Given the current threat landscape, Finanstilsynet expects that security testing will be given the necessary attention by the institutions in the future. |
ID theft
Several institutions state that the risk of ID theft remained one of the highest risks for their operations in 2024. The risk associated with inadequate measures to prevent an attacker from taking over and misusing a customer's and/or a system user's ID is the issue most respondents have assessed the risk as high and/or increasing. The risk associated with inadequate measures to prevent an attacker from taking over and misusing a customer's and/or a system user's ID is assessed as high and/or increasing by the highest proportion/number of respondents. More than one-third responded that the risk is assessed as high. In addition, several of those who did not assess the risk as high stated that it is deemed to be increasing. The overall risk is also considered to be on the rise. Particular reference is made to the risk of social engineering, where customers share information that can be misused, as well as to major fraud losses in 2024. The institutions report that they maintain a strong focus on control and that they implemented a number of anti-fraud measures during the year.
|
Finanstilsynet notes that several institutions implemented a number of anti-fraud measures in 2024. Finanstilsynet finds that the institutions have made both an appropriate and important choice and expects them to continue to focus on this during the current year in light of the increasing incidence of fraud. |
Internal misconduct
Feedback suggests that institutions remained vigilant about this threat in 2024. Well over half of the institutions considered the risk of inadequate control of internal irregularities and misconduct scenarios to be moderate, which is an increase from 2023, when the majority assessed the risk as low. For 2023, two-thirds assessed the risk of inadequate logging and reporting as low, while less than half made the same assessment for 2024. The institutions emphasise that various measures have been established to mitigate risk, including dual control ('four eyes principle') wherever possible, and stricter access management.
|
Finanstilsynet notes that although the institutions assess the risk as higher for 2024 than for 2023, many still assess the risk as low. Some threat reports indicate that criminals are becoming increasingly professional and that professional facilitators and insiders are selling their services to criminal organisations. The threat of self-motivated insider dealing is also highlighted. For this reason, Finanstilsynet emphasises the importance of remaining attentive to the risk of internal fraud and the need for effective control mechanisms to prevent and detect such activities. |
ICT support for anti-money laundering and counter-terrorist financing
ICT support for anti-money laundering and counter-terrorist financing has previously been an area where institutions have assessed the risk as significant. For 2023, the institutions assessed the risk as somewhat reduced. The positive trend continued for 2024, and the institutions now assess the risk as generally low or moderate.
For 2024, the institutions generally assess the risk as moderate that ICT systems do not provide a comprehensive view of customers, customer relationships and customer behaviour. The assessment was the same the year before. However, the proportion considering the risk to be low fell slightly from 2023 to 2024, when just under one in three assessed the risk as low. When it comes to disclosing suspicious transactions, one-third of the institutions assess the risk as low, which is a decrease from 2023, when approximately 40 per cent made the same assessment.
However, the institutions still believe that there is a risk that their transaction monitoring systems will not capture all payment transactions that should be investigated further, and more than six out of ten assess the risk as moderate or high. This is on a level with the previous year. However, a higher proportion, almost three-fourths, assess the risk of their systems failing to recognise suspicious patterns over time as moderate or high.
Institutions' trust in sanction screening systems has increased. For 2024, almost four out of ten institutions, compared to three out of ten in 2023, assess the risk as low that the sanction screening system lacks high precision in matching listed individuals and institutions. Only one bank considers the risk to be high in 2024.
|
Finanstilsynet notes the positive trend in the institutions' assessment of ICT support for anti-money laundering and counter-terrorist financing. In Finanstilsynet's experience, however, there is still risk associated with adverse incidents in the transaction monitoring systems. Finanstilsynet has also noted that almost three out of four assess the risk of the systems failing to recognise suspicious patterns over time as moderate or high, although they also consider the ICT systems to provide increasing support. Finanstilsynet expects the institutions to follow up this. |
5. Risk associated with new technology
5.1 Risk associated with the use of artificial intelligence
The use of artificial intelligence (AI) in the financial sector offers many opportunities but also entails significant risks. Failures in AI systems can result in major financial losses and harm to the institution's reputation. AI systems are also attractive targets for hackers due to AI's use of large amounts of data, which presents an increased risk of data breaches and hacking.
Errors in algorithms or biases in training data can, among other things, lead to incorrect investment decisions or credit assessments, flawed analyses, misleading customer communication or inaccurate fraud detection. This can lead to major financial losses for institutions and investors, as well as dissatisfied customers and loss of trust in the technology. The institution's reputation may also be harmed. A lack of explainability can further make it difficult to understand how a decision was made. This can create regulatory and ethical challenges and increase the risk of sanctions and compensation claims. The use of such systems must therefore be in accordance with requirements for both explainability and verifiability, including retrospective explainability. This means that if the technology is used to assess loan applications, a rejection, an approval, an assessment of the credit limit or an interest rate determination must be explainable, even retrospectively. In addition, the system must give the same response for equal inputs. When used in anti-fraud work, for example, it must be possible to explain why a transaction has been stopped. To minimise these risks, thorough testing, ethical development of AI and continuous monitoring of the systems are important.
Institutions must establish robust security measures to protect AI systems against ICT security threats such as data breaches, hacking and data manipulation that can affect the system's performance. This includes regular security updates, data encryption, access control and security audits. When maintaining AI systems, including during updates, proper governance is required to prevent the introduction of errors and vulnerabilities. Regular security testing and continuous monitoring of the results provided by the AI system are essential for identifying and managing security threats.
Where the use of AI systems is part of the institution's processes, technical preparedness and operational continuity are necessary to secure the institution's service deliveries. Backup solutions and redundancy must be established to ensure sufficient continuity if technical problems/ disruptions occur in the AI system. To ensure the preparedness of the AI system, regular testing
of alternative procedures (preferably manual), backup systems and contingency plans should be carried out to check whether the institution can handle operational disruptions in the AI system.
EU regulations such as the AI Act and the Digital Operational Resilience Act (DORA) set requirements for AI systems and focus on protecting customer rights, ensuring ethical standards and preventing discrimination. Institutions must, by managing and controlling the development and use of AI systems, ensure compliance with these regulations, which includes avoiding bias and discrimination in the model's outcomes.
In order to mitigate the ICT risks associated with the use of AI systems, institutions must continuously monitor, control and revise the systems to ensure that they function as intended and in accordance with applicable regulations. Furthermore, institutions must ensure adequate data quality and integrity and establish clear guidelines for procurement, development, implementation and use. Responsible data governance, adherence to ethical guidelines, ensuring necessary explainability and verifiability, and proactive measures against data misuse are crucial to maintaining trust in AI systems and ensuring that they deliver value to the institution.
In 2024, Finanstilsynet surveyed insurers' use of advanced technology, such as AI.18)
5.2 Threats related to quantum technology
Quantum technology is based on the principles of quantum mechanics (the description of the structure and dynamics of fundamental particles) and, among other things, provides the opportunity to build so-called quantum computers with far greater computing power and capacity than even today's supercomputers.
The technology is still in its early stages but is believed to have great potential for the application of ICT in society. At the same time, the technology also poses threats as its vast computing power can be used for malicious purposes. For example, such computers can be used to decrypt sensitive content and data protected by cryptographic algorithms, which increases the vulnerability to cyberattacks and fraud in banks and other systems.
This technology is estimated to be ready in five to fifteen years, which is between 2030 and 2040. However, technological breakthroughs may lead to the technology becoming available earlier. This underlines the need to monitor developments closely and for institutions to have a long-term strategy for ICT procurement.
Expectations surrounding the emerging quantum technology may already have consequences, for example in the form of a strategy of 'harvest today, decrypt later'. Algorithms used in trading, risk analysis and portfolio optimisation could be subject to theft and manipulation, and sensitive customer data in the insurance industry could also be at risk. This may result in financial losses and erosion of customer trust and have legal repercussions.
To protect themselves against the threats posed by quantum technology, financial institutions should adopt new encryption algorithms as they are developed. This involves upgrading to quantum-safe security equipment, including quantum-safe number generators (QRNGs19)), which generate random numbers necessary for secure encryption. Furthermore, they should also adopt quantum-safe key distribution (QKD20)), which ensures secure transmission of encryption keys and quantum-safe hardware.
As with other threats arising from new technology, it will be necessary for institutions to ensure that they are equipped to meet the security challenges posed by malicious use of quantum technology. Potential measures could include investing in training, developing response strategies and collaborating to establish standards for uniform and effective implementation across the financial sector.
Continuous monitoring of developments within quantum technology is necessary to anticipate new threats that may arise from its use, adapt security strategies and safeguard ICT infrastructure. At the same time, assessments must be made regarding what information may be at risk.
6. Fraud
Payment service providers, i.e. banks, credit institutions, electronic money institutions and payment institutions, and branches of such institutions headquartered in other EEA states, report fraud statistics to Finanstilsynet every six months. The results and trends are presented in separate reports on Finanstilsynet's website. Some key findings from 2024 are described below.
6.1 Fraud in 2024
In 2024, there was a significant increase in total losses compared to previous years, as shown in table 6.1. There was a rise in losses from 2023 to 2024 of NOK 299 million, representing approximately 32 per cent. The largest increase in losses was observed for card payment fraud at around 54 per cent. For fraud involving account transfers, there was an increase of about 22 per cent, compared with approximately 64 per cent in 2023. Although the changes in fraud-related losses involving card payments and account transfers were approximately at the same level in monetary terms in 2023 and 2024, the percentage increase for card payment fraud in 2024 indicates a significant shift. For 2023, fraud involving account transfers showed the highest percentage increase. When measured as a proportion of total transaction value, total losses amount to 0.0020 per cent, which is an increase compared with previous years.
Table 6.1 Total losses from fraud. Amounts in NOK million.
|
Period |
Fraudulent transactions – account transfers (online banking, etc.) |
Fraudulent transactions with card payments reported by the card issuer |
Total losses |
Losses in per cent of total transaction value |
|
2024 |
790 |
437 |
1,227 |
0.0020% |
|
2023 |
648 |
281 |
929 |
0.0014% |
|
2022 |
395 |
219 |
614 |
0.0013% |
|
2021 |
346 |
162 |
508 |
0.0014% |
Source: Finanstilsynet
Statistics show that reported fraud-related losses have doubled over the last two years, from
NOK 614 million in 2022 to NOK 1,227 million in 2024.
Market participants are continuously working on anti-fraud measures to detect and prevent fraud. Banks intercept a high percentage of fraud attempts, and in total, prevented losses amounting to NOK 2,964 million in 2024, with account transfers accounting for NOK 891 million and card payments for NOK 2,074 million. This is an increase of 43 per cent from NOK 2,072 million in 2023.
In addition to stopping initiated fraudulent transactions, Finanstilsynet is aware that institutions also prevent fraudulent activity before a transaction is initiated, and these cases are not included in the reported figures. This means that the total scope of fraudulent activity prevented by the banks is higher.
On 1 August 2024, the European Banking Authority (EBA) and the European Central Bank (ECB) published a report showing developments in losses from payment fraud for the first and second half of 2022 and the first half of 2023.21) The figures for the first half of 2023, table 1, show that the proportion of losses in Norway is low compared with most other EEA countries.
6.2 Social engineering
Social engineering22) is still the most common form of fraud, and according to figures reported to Finanstilsynet, losses came to NOK 667 million in 2024. This is a significant increase of 42.5 per cent from 2023, when losses totalled NOK 468 million. For card payment fraud, the increase was 260.3 per cent, while it was 29.6 per cent for account transfer fraud. However, losses were lower for the second half than for the first half of the year, amounting to NOK 307.3 million and
NOK 359.7 million, respectively.
Table 6.2 Losses from social engineering fraud. Amounts in NOK million.
|
Social engineering, type of payment |
2022 |
2023 |
2024 |
|
Card payments |
21.5 |
26.2 |
94.4 |
|
Account transfers |
268.8 |
441.8 |
572.6 |
|
Total |
290.3 |
468.0 |
667.0 |
Source: Finanstilsynet
Social engineering has also become more sophisticated with the use of artificial intelligence (AI). Attackers can use AI to analyse large amounts of data and tailor phishing attacks that are harder to detect. AI can also generate fake, but convincing, messages and profiles, making it easier to trick individuals into revealing sensitive information.
AI can further be used to automate social engineering, which increases the scale and effectiveness of such attacks and helps criminals quickly make changes to their modes.23) This creates challenges for security protocols, which must be adapted to handle these new threats. Institutions must therefore invest in advanced security measures and continuously update their defence mechanisms to protect themselves against the increased risks associated with AI and social engineering.
Deepfake technology uses artificial intelligence to create manipulated images, audio recordings and videos that appear real. According to a report from Signicat,24) criminals have used artificial intelligence in 42.5 per cent of fraud attempts detected in the financial sector. This makes deepfakes the most common form of digital identity fraud currently experienced by bank customers. Three years ago, deepfakes were not among the three most common types of digital identity fraud.
One method of social engineering that increased significantly in 2024 is fraudsters calling or visiting victims at home, pretending to be from the bank or the police. The fraudsters claim that the victim is at risk of being defrauded and ask them to transfer their money to a 'safe account' that the fraudsters themselves control. In some cases, the fraudsters have also arranged physical meetings with the victim to make them execute payments or to take the victim's bank card. This type of fraud often involves large amounts of money. Banks, the police and other public or well-known actors all point out that they will never call customers and ask them to provide login information or transfer money to other accounts.
6.3 Anti-fraud measures
Banks bear significant financial responsibility for fraud in their systems, which serves as an incentive for implementing preventive measures. The industry follows recommendations from Finance Norway and the Bank Anti-Fraud Expert Committee to prevent, detect and follow up fraud.25)
The measures vary based on developments in the fraud landscape and include compliance with industry standards and checklists. Some measures are general, while others are aimed at specific types of fraud. This reflects that some measures have been in progress for a long time, while others are new and still under development. The main focus is on preventing fraud to reduce the number of victims. Many measures are also about detecting and stopping fraud as it happens. In cases where fraud occurs, follow-up measures are in place.
The fraud situation in the Nordic countries has many similarities, and several banks operate across the region. Finance Norway recommends closer and regular cooperation between banks to improve information sharing and ensure effective cross-border cooperation in the Nordic region.
Technological developments within automation and AI provide many new opportunities but also create vulnerabilities when fraudsters exploit these technologies. In order to stand up to the fraudsters and combat cyber fraud, it may be valuable to have closer cooperation between banks, social platforms, the e-commerce sector and public agencies, both nationally and internationally. This will help ensure that several measures can be aligned and have a greater impact in the fight against fraud.
Several banks have adopted anti-fraud systems that use AI and machine learning to classify normal user behaviour. At the same time, the use of instant payments makes anti-fraud work challenging, as new EU regulations require that such payments be made in euros. This is about finding a balance between efficiency and security, so that payments are not only simple and effective, but also secure.
Payment card scheme providers are also working on measures to make card payments more secure and to prevent fraud. Among other things, Mastercard aims to tokenise all payment cards by 2030 as part of its efforts to develop new solutions that support growth, profitable business operations and sustainable societies.
In January 2024, the authorities called on mobile network companies to cooperate more closely to prevent more SME-based fraud attempts. A digital shield has been established that enables the blocking of fraud attempts from hijacked numbers at other Norwegian mobile operators. Norway
is the second country in the world to introduce such solutions, which has ensured a significant reduction in the misuse of Norwegian mobile numbers.26)
One of the EU's priority tasks is to introduce new rules, including through the Instant Payment Regulation (IPR). The regulation requires payment service providers to establish solutions that enable payers to verify payees, which could make it more difficult to pursue current fraud tactics.
The EU's ongoing revision of the second Payment Services Directive focuses on measures that can help combat fraud, including the sharing of information, subject to certain conditions, in cases of suspected fraud. Based on an analysis of reported fraud data, the EBA published an opinion on 29 April 2024 with recommendations to further strengthen provisions related to anti-fraud in the proposed Payment Services Regulation (PSR) and the Third Payment Services Directive (PSD3).27)
6.4 Collaboration to combat financial crime
Increased collaboration related to the sharing of information and intelligence between institutions, between authorities and between institutions and authorities could strengthen the fight against fraud, money laundering and terrorist financing in the financial sector. Financial institutions can share data on phishing methods, malware attacks, card fraud patterns, identity theft attempts and suspicious transactions related to money laundering and terrorist financing, while authorities can share national and international threat intelligence from investigations and regulatory efforts, including insight on fraud and anti-money laundering.
Through increased collaboration, it is possible to build platforms for the rapid exchange of intelligence that uncover fraud techniques, track criminal networks and identify money laundering patterns, while institutions also work together to develop robust 'know your customer' (KYC) procedures and trace illicit financial flows across borders. The draft Payment Services Regulation (PSR) includes provisions on the exchange of information related to anti-fraud efforts, including information about payees.
Collaboration can enable a better proactive response, such as blocking threats and fraud and money laundering attempts before they escalate and can contribute to the establishment of joint solutions for analysing fraud and money laundering data. This can significantly enhance the efficiency of the sector's efforts to combat criminal activity.
In autumn 2024, together with the Norwegian Data Protection Authority, Finanstilsynet invited institutions in the financial sector to participate in the agencies' regulatory sandboxes to explore possibilities for data sharing in the fight against financial crime. The purpose of the projects is to explore such possibilities within current regulations, identify any obstacles and assess any needs for regulatory development. Five projects that raise interesting issues and have the potential to generate valuable new insights for the fight against financial crime have been admitted to the sandbox.28) Three of the five projects are related to fraud and scams and two to anti-money laundering.
7. Incidents
Serious failures in ICT systems can have severe consequences for the financial infrastructure. According to the ICT Regulations, operational and security incidents are required to be reported to Finanstilsynet without undue delay. Incident reporting should help Finanstilsynet quickly gain a correct understanding of the incident, including its scope and severity. In addition, the reporting plays a crucial role in ensuring an accurate and timely assessment of the risk level in the financial sector and in uncovering patterns and connections that may be challenging for individual institutions to detect.
The way the institution, including its service providers, handle the incident to ensure rapid recovery, relevant actions towards affected customers and relevant preventive measures is nevertheless most important.
Institutions reported 365 ICT incidents to Finanstilsynet in 2024, This is a slight decrease from the previous year, see figure 7.1. Out of the 365 reported incidents, 20 were security incidents, while the rest were operational incidents.29)
Fig. 7.1 Number of reported ICT incidents
For more detailed information on the data used, see appendix 4.
Source: Finanstilsynet
Again in 2024, there were many incidents that affected several financial institutions at the same time, but fewer than in the previous year. One incident on 21 May, with duplicate eInvoice payments and direct debits, affected a large volume of transactions across a number of banks. The incident was subject to special follow-by Finanstilsynet, see section 7.9. There were few operational incidents that caused payment services to be inaccessible for more than three to four hours. One bank was subjected to extensive and prolonged denial of service attacks (DDOS) that for periods reduced access to payment services.
7.1 Security incidents
There were 20 reported security incidents in 2024, which is slight increase from the previous year. Seven of the incidents were denial of service attacks (DDoS), mainly reported by banks. These attacks mainly took place in September and October, when several banks were intermittently targeted by DDoS attacks with a different modus operandi than previously observed. In most cases, the consequences of such attacks were limited, but for one bank the consequences were serious at times, with reduced access to the bank's payment and other customer services. Some of the attacks stood out in terms of complexity and appeared more sophisticated, originating from IP addresses located in Nordic countries. This made the work on countermeasures more challenging.
Other security incidents, mainly reported by small financial institutions, concerned attacks on Norwegian or foreign subcontractors in the value chain. Vulnerabilities in software were exploited to gain access to the subcontractor's systems, and in several cases, ransom was demanded to unlock the systems or refrain from publishing or stealing data. The incidents had major consequences for several small financial institutions.
7.2 Office 365 vulnerabilities
One Adversary-in-the-Middle (AiTM) attack was reported. By way of phishing, the attacker managed to compromise the two-factor authentication of an employee's (CEO) login to the cloud-based Microsoft Office 365 platform. In the period before a new two-factor authentication was required, the attacker had the same access rights as the employee to SharePoint, Teams, email, etc. and could misuse the accesses in various ways. In this case, the attacker used the employee's contact lists to send phishing emails as well as to read emails and attempt to edit attachments. The attack was discovered after three days. This type of attack was described in the Risk and Vulnerability Analysis for 2023. At the time, this was quite new. Since then, AiTM attacks have grown in scope and are often organised through separate campaigns using different methods (attack vectors). The attacks do not only target the financial sector. Attacks on Norwegian financial institutions have been largely unsuccessful. Just like the incident reported in 2023, the incident in 2024 was reported by a small financial institution.
7.3 Crowdstrike
Crowdstrike is a security platform for Windows with a wide global reach. On 19 July 2024, Crowdstrike released a new version of an antivirus software that turned out to contain a bug. Computers on which this version was installed ended up displaying a 'blue screen' and could not be restarted. It quickly became clear that this was an operational incident and not an attack. After a few hours, Crowdstrike reported that they had solved the problem.
Six financial institutions reported the incident to Finanstilsynet. All of these were affiliated with European groups and most of them were from the securities sector. It was the workstations of employees that were affected, not the production systems. The incident did not have serious consequences for any of the institutions, but some institutions spent several days reinstalling software.
7.4 Lack of or inadequate acceptance testing of changes carried out by service providers
Again in 2024, a number of incidents were reported concerning errors in solutions following planned changes implemented by service providers. These included errors in the tokenisation of payment cards and in the codification in the systems for uncovering money laundering and terrorist financing, amount limits, etc. These errors should have been detected during the testing process, which underscores the importance of thorough testing by service providers, acceptance testing and internal controls within the institutions. Each institution is responsible for its systems and services, regardless of whether they were developed and are operated by the service provider or the institution itself.
|
Finanstilsynet expects the institutions to follow up suppliers' change processes and to implement measures related to both testing and acceptance of changes, as well as monitor that data processing does not result in errors or deficiencies. |
7.5 Incidents in systems for detecting money laundering and terrorist financing
In 2024, there were 16 reported incidents concerning deviations in institutions' electronic solutions for transaction monitoring to detect money laundering and terrorist financing. Several of the reported incidents were caused by the same error from a common service provider. There were serious non-conformities related to deficiencies in the sanction screening. Furthermore, errors in the model that estimates customers' money laundering risk and errors in the monitoring of credit card transactions were reported.
7.6 Incidents by type of institution
Figure 7.2 provides an overview of the number of incidents by type of institution, divided into operational incidents and security incidents. The incidents are described in further detail below.
Figure 7.2 Reported incidents in 2024 compared to 2023 by type of institution
Source: Finanstilsynet
Banks
The incident that occurred on 21 May stood out as particularly serious among the incidents that affected banks in 2024, see section 7.9. Approximately 10 per cent of the incidents reported by banks concerned this. There were fewer operational disruptions related to instant payments than in the previous year. A few operational deviations revealed that some components still lack redundancy, and several operational deviations were caused, among other things, by insufficient capacity and certificate monitoring. Nevertheless, there were few operational incidents that seriously affected the availability of payment services. On the other hand, severe DDoS attacks targeted several banks, and for one bank, these attacks intermittently affected the availability of services. See more about security incidents above. There were also a number of incidents relating to errors in various applications following changes, including changes to the systems for detecting money laundering and terrorist financing. See more about inadequate acceptance tests above.
Payment institutions
Only six incidents were reported by payment institutions. One of these was a serious operational incident in January 2024 that resulted in the payment services not functioning for approximately five hours.
Finance companies
Finance companies reported one security incident concerning an internal irregularity at a subcontractor and two incidents related to failures in the systems for detecting money laundering and terrorist financing.
Securities
There were fewer incidents affecting Euronext Securities Oslo (VPS) and the regulated marketplaces than in the previous year. There were no reports of delays in the actual securities settlement.
VPS was affected by an incident on 2 September in which a planned reorganisation of the interbank settlement system failed, resulting in a delay in the transfer of money between banks and thereby payment of dividends and interest from VPS. Other incidents related to VPS and the regulated marketplaces were incorrectly registered shares, errors during system upgrade testing, parameter changes implemented either incorrectly or ahead of schedule, failures in reading backups, miscalculations of indices and reporting errors. Four firms in the securities sector reported problems as a result of the Crowdstrike incident. The remaining reports on operational incidents in the securities area were dominated by problems with access to online trading of financial instruments and brief service disruptions related to services on the marketplaces, as well as missing audio recordings. Two security incidents were reported in the securities area, both of which were ransomware attacks targeting subcontractors.
Insurers
Due to the limited number of reports from insurers in previous years, Finanstilsynet questioned the industry's understanding of the reporting obligation under the ICT regulations and sent letters to insurers at the beginning of 2024 with examples of incidents to be reported. From 2023 to 2024, the number of reports from insurers increased from six to 21. Of these, there were six reports on security incidents, including one DDoS attack, one AiTM attack, two ransomware attacks, one internal misconduct incident and one phishing incident due to inadequate email spam filtering. Operational incidents included lack of access to telephone and online customer services, delayed payments, unavailability of case processing systems, confidentiality breaches and identified vulnerabilities. Four reported incidents concerned duplicate payments where the insurer represented the recipient in the Avtalegiro (direct debit) or eInvoice payment transactions on 21 May, see section 7.9.
Debt collection agencies
Debt collection agencies reported operational incidents that occurred after system changes, resulting in discrepancies in the case processing workflow. The discrepancies were related to errors in payment deadlines or invoiced amounts, or breaches of confidentiality, allowing customers to view other customers' information. One incident of duplicate payments was also reported, where a debt collection agency was the recipient in the direct debit or eInvoice payment transactions on 21 May, see section 7.9. Two security incidents were reported by debt collection agencies. Both were attacks on subcontractors.
7.7 Analysis of incidents as a measure of availability
The reported incidents vary in severity. For incidents that resulted in reduced availability of payment services and customer services, Finanstilsynet has evaluated and weighted the incidents based on the timing and duration of the disruption, the number of affected institutions, the number of impacted customers, and whether alternative services were available to meet customer needs. When considering alternative services meeting customer needs, the availability of web-based services is assessed if mobile app services do not function. The fact that the alternatives may not offer the same range of services is also taken into account, for instance that mobile payment solutions often do not provide all the services available through web-based solutions. The weighting of incidents produces an index shown on the vertical axis in figure 7.3. The findings are compiled into a time series to track developments over time.
Figure 7.3 shows that the availability of payment services and customer solutions is assessed as largely unchanged from 2021 to 2024. The overall availability of services in 2024 is considered satisfactory in line with the three preceding years.
Figure 7.3 Incidents causing reduced availability for users. Weighted by estimated impact*
* The vertical axis scale is an index based on the weighting of each incident. A lower index value indicates a lower occurrence of operational disruptions with consequences for users. For more detailed information on the data used, see appendix 3.
Source: Finanstilsynet
The figure shows an increase, again in 2024, in deviations within the category 'Clearing and settlement', which are deviations occurring after the payer has registered the payment. These include issues related to duplicate transactions, reservations not processed at the correct time, and banks failing to meet clearing deadlines. These deviations can result in incorrect available account balances for customers, making their funds inaccessible.
7.8 Incidents related to dedicated PSD2 interfaces
Both account servicing payment service providers and payment service providers are required by regulations to report to Finanstilsynet any issues with dedicated interfaces for third-party service providers' access to customers' payment accounts. The threshold for such reporting is lower than what follows from the requirements of the ICT regulations. The banks generally reported any problems with the interfaces, whether related to availability or functionality. One bank provides weekly updates on its dedicated interface, including any issues with availability or functionality. Third-party service providers also reported observed downtime and lack of functionality in banks' dedicated interfaces. Lack of functionality was specifically addressed with account servicing payment service providers based on reported deficiencies. Finanstilsynet has, on the basis of its follow-up of reported deficiencies, published clarifications and explanations regarding the regulations.
7.9 Duplicate eInvoice payments and direct debits
The incident on Tuesday, 21 May 2024 resulted in duplicate eInvoice payments and direct debits. Due to its scope and severity, it was subject to special follow-up by Finanstilsynet. The incident was caused by an error in a service provider's operational calendar that resulted in incorrect processing of payment files in connection with public holidays before and after a weekend. The incident affected a large volume of transactions across a number of banks. The incident resulted in incorrect balances on customer accounts, both on the sender and on the recipient side, and it took several days before all duplicate transactions were reversed.
Finanstilsynet considers incidents resulting in incorrect balances, where customers cannot rely on their account status and account statements, to be particularly serious. In this case, the scale of the incident and the duration of the correction process also gave cause for concern. Finanstilsynet therefore decided to send identical letters with questions to all banks and hold meetings with relevant players in the value chain to get a complete overview of the root cause and insight into the industry's measures to prevent a similar incident from happening again.
Through the service provider's incident report, Finanstilsynet has noted that the root cause of the incident was that the operating calendar was not updated correctly in accordance with public holidays for 2024. In connection with the weekend of 18–19 May, which was preceded and followed by public holidays, two jobs were therefore run with the same transactions.
Based on the banks' responses, it appears that many of them had not carried out a risk assessment of the service provider's reversal/correction procedure, but that several of them have decided or are considering doing so in the future. A number of banks also responded that they do not check the service provider's operational setup.
Finanstilsynet therefore questions whether the banks, as part of their vendor management, are sufficiently involved in the quality assurance of the service provider's operating calendar, and whether they make sure that the service provider has adequate system alerts and handles such alerts in an appropriate manner.
Finanstilsynet also received reports from financial institutions representing the receiving side of the duplicate transactions, revealing that there are a number of differences in procedures and system support for correcting duplicate transactions. Finanstilsynet has also held talks with parties that assisted in making corrections following the incident, focusing in particular on challenges with correcting OCR/KID transactions.
Finanstilsynet expects the banks to ensure that they have a sufficient overview of vulnerabilities throughout the value chain to be able to implement relevant measures. This also applies to the receiving side, where it is important that banks fulfil their responsibility by informing their customers so that they too can take the necessary measures. Furthermore, Finanstilsynet expects the banks, across the value chain and any outsourcing arrangements, to identify and implement measures to prevent a corresponding incident with similar consequences from occurring and to strengthen the correction/recovery process. In Finanstilsynet's opinion, this will require collaboration across the value chain.
8. Assessment of the financial infrastructure and institutions' IT operations
8.1 The financial infrastructure is robust
Finanstilsynet considers the Norwegian financial infrastructure to be robust. In 2024, there were no incidents with consequences for financial stability, but a few serious incidents could have led to significant disruptions if they had not been resolved quickly.
The clearing and settlement systems were affected by a number of serious incidents that led to delays in the execution of payments. However, regularity was generally satisfactory. The regularity of the communication with the international payment and securities transfer notification network, SWIFT30), and the international settlement system, CLS31), was good.
Overall, slightly fewer serious incidents were reported in 2024 than in 2023. The proportion of security incidents was somewhat higher than in 2023. Nonetheless, the institutions' services appear to be generally well protected against attacks, although some security incidents at service providers in 2024 had major consequences for the affected institutions. Slightly fewer operational incidents were reported in 2024 than in 2023. However, some of the incidents attracted considerable attention, including one that involved a breach of integrity due to incorrect account balances, see further description under section 7.9. The institutions' operational stability and the availability of payment services and other customer services nevertheless remain consistent with the past three years and are considered to be satisfactory, see section 7.6.
Attacks on the financial infrastructure appear to be fewer than in previous years, but the extent of cybercrime in the form of fraud continues to increase. Cyberattacks are usually prevented before institutions and their customers suffer any consequences. So far, cybercrime targeting financial infrastructure has not led to systemic crises or severe incidents at institutions in the Norwegian financial sector.
Institutions need to recognise that the cyberthreat landscape is constantly changing, partly as a result of criminals refining existing or creating new methods and interacting in new ways, and as a result of geopolitical changes, Russia's war of invasion in Ukraine, the conflict between Israel and Hamas and the conflict between India and Pakistan. Vulnerabilities and security flaws pose a risk of being exploited by criminals and risks of information leakage or unauthorised changes in the systems and infrastructure of institutions or their service providers.
Cyber incidents generally occur suddenly, leading to a breakdown in the financial infrastructure and having far-reaching societal consequences. In order to reduce the likelihood and consequences of deviations, organisations must continuously strengthen ICT security in general by implementing measures to ensure stable operating solutions, prevent cybercrime and handle incidents quickly and efficiently. This includes crisis solutions and preparedness, recovery plans and IT security work, including defences against cybercrime. Threat-led penetration tests (TLPT) conducted in accordance with TIBER-NO have demonstrated a high level of security within the organisations.
8.2 Risk associated with vulnerabilities in institutions’ ICT operations
Figure 8.1 summarises Finanstilsynet's assessment of the most critical vulnerabilities in the financial sector. These vulnerabilities are classified based on the likelihood of a severe adverse incident occurring and the severity of the resulting consequences for each institution. The observations and assessments underlying this classification are detailed in table 8.1 and further discussed in appendix 2.
In this year's report, Finanstilsynet also regards vulnerabilities related to institutions' or their service providers' defences against cybercrime as the most significant risk associated with their use of ICT, with the overall risk still deemed to be high and slightly increasing. Examples of such vulnerabilities are that serious security flaws are not promptly patched or that applications integrated by third parties (the value chain) lead to adverse incidents. The cyberthreat landscape suggests that such vulnerabilities will be exploited by malicious actors, potentially having severe consequences.
Vulnerabilities related to access management, governance model, internal controls and vendor management also represent key risks, with the overall risk considered to be medium to high. The risk associated with the governance model and internal control is considered to be somewhat higher than the previous year. The risk associated with inadequate vendor management is considered to be somewhat lower, while the risk associated with institutions' access management is considered to on a level with last year. Such vulnerabilities may be due to the risk management function not having the required expertise to fulfil its second line function in the ICT area or to significant deficiencies in service providers' internal control not being detected by the institution.
Risk associated with vulnerabilities in institutions' preparedness and crisis management, as well as geopolitical factors, is also considered moderate to high. For vulnerabilities related to institutions' change management, information leaks, ICT operations, skills and skills management and data quality, the risk is assessed as moderate. The risk associated with geopolitical developments is considered to have increased, particularly in light of shifts in US policy resulting from the new presidency. The risk associated with change management is also considered to have increased due to both the underlying causes of incidents and the identification of deficiencies in institutions' change processes during inspections. The risk associated with information leaks is assessed as somewhat lower in this year's report.
Figure 8.1 Finanstilsynet's assessment of vulnerabilities and risks for 2024
Source: Finanstilsynet
Table 8.1 Vulnerabilities that could represent a risk of adverse incidents
|
Area
|
Vulnerabilities that could represent a risk of adverse incidents (The degree of risk, probability and consequence are shown in figure 8.1) |
Trend |
|---|---|---|
|
Governance model and internal control
|
An inadequate overview of which controls are included in the institution’s internal control environment and how the controls should be performed, monitored and audited may result in factors that represent an operational risk not being identified and risk-mitigating measures in line with the institution’s risk tolerance not being implemented. |
Increasing |
|
Skills and skills management |
A scarcity of resources in Norway within operations, architecture, security and new technology, as well as inadequate skills management, may lead to institutions being unable to meet current and future skill needs. Problems and errors that occur may be difficult to resolve. Dependence on foreign assistance may increase. |
Unchanged |
|
Vendor management
|
Complex supply chains, with multiple service providers and subcontractors in the value chain, demanding cooperation models (strategic, administrative and operational) and a lack of expertise may result in weaker monitoring and control over critical and outsourced ICT services. |
Decreasing |
|
Cybercrime |
Inadequate security testing, security updates, training and awareness raising among employees, and insufficient monitoring of activities in its own technical infrastructure, including networks and systems, may result in criminals inflicting damage on the institution through digital attacks. Fraud related to the use of financial services can also inflict losses on the institution. |
Increasing |
|
Information leaks |
Inadequate information classification, including documentation, and controls for monitoring information that is sent by email, copied to external storage devices or copied to private cloud services may cause the institution or its customers damage if unauthorised people get their hands on the information. |
Decreasing |
|
ICT operations
|
Complex integration between systems from different service providers, integration between old and new systems, multiple integration points between systems, increased functionality in self-service channels and increased use of cloud services may result in challenges in maintaining stable and secure operations. |
Unchanged |
|
Emergency preparedness and crisis management |
Inadequate analyses of the consequences of a crisis, inadequate training and exercises in crisis management, shortcomings in disaster recovery solutions/backup solutions and inadequate backup solutions may result in challenges for institutions when it comes to maintaining critical ICT services in the event of severe disruptions at operating locations. |
Unchanged |
|
Geopolitical conditions
|
Geopolitical factors or interruptions in communications with other countries, where service providers are prevented from maintaining deliveries of critical ICT services from abroad, may result in challenges in maintaining stable and secure operations. |
Increasing |
|
Change management
|
A fast pace of development, where quality is sacrificed at the expense of time, may result in functional errors in applications and systems, and in security flaws not being identified. Inadequate control of changes to configurations within operations may result in interruptions to critical business processes and the institution being exposed to cybercrime. |
Increasing |
|
Access Management
|
Inadequate control and monitoring of extended access rights for employees and service provider personnel may harm the institution and its customers due to information leaks and deliberate or unintentional operational errors |
Unchanged |
|
Data quality
|
Deficiencies or errors in data may result in analyses and controls being performed based on incorrect or insufficient information. This may include errors in credit ratings, errors in controls aimed at detecting money laundering or fraud, errors in risk assessments and errors in monitoring operations. |
Unchanged |
Source: Finanstilsynet
Notes:
1) On-Prem (On-Premise) means that the software and all necessary infrastructure are installed on the institution's own servers, physically located on the institution's premises.
2) Systemic cyber risk 2020, Mitigating systemic cyber risk 2022, Macroprudential tools for cyber resilience 2023
3) Finanstilsynet’s news item 21 October 2021: Norges Bank and Finanstilsynet establish framework for testing of cybersecurity in the financial sector (TIBER-NO) (in Norwegian only). The TIBER-NO framework is based on the European Central Bank’s Framework for Threat Intelligence-based Ethical Red Teaming (TIBER-EU).
4) The TIBER-NO forum is an established collaboration arena for companies that perform TLPT testing according to the TIBER-NO framework.
5) See the Financial Markets Report 2023, section 4.2.2 (in Norwegian only)
6) Finanstilsynet has been designated as sectoral response environment (SRE) by the Ministry of Finance.
7) See topic page on BFI
8) Advice on self-preparednessDirektoratet for samfunnssikkerhet og beredskap (DSB) – Egenberedskapsråd
9) NOU 2023:17) – Now it's serious (in Norwegian only)
10) Norwegian National Security Authority (NSM) Risk 2022, page 29 (in Norwegian only)
11) See the Financial Markets Report 2021, page 25 (in Norwegian only)
12) NOU 2024:21 – Safe and simple payments for everyone (in Norwegian only)
13) 'Stand-in processing'
14) Working group proposes measures to strengthen emergency preparedness in the payment system (in Norwegian only)
15) DevOps is a methodology that connects people, processes and automation to streamline development and operational processes for quicker and more reliable deliveries.
16) An automated change is a process where software or systems make changes without human intervention. This may include updates, configuration changes or other adjustments that are predefined and performed automatically.
17) On-Prem (On-Premise) means that the software and all necessary infrastructure are installed on the institution's own servers, physically located on the institution's premises.
18) Survey of insurers' use of advanced technology (in Norwegian only)
19) Quantum Random Number Generation
20) Quantum Key Distribution
21) EBA's and ECB's fraud report 2024
22) Social engineering is fraud where payers are manipulated into initiating the fraudulent transaction themselves.
23) How fraudsters use artificial intelligence in banking scams and Inside the fraud operations centre (in Norwegian only)
24) Signicat's report: The Battle Against AI-Driven Identity Fraud. 20 February 2025
25) Norwegian banks' fight against fraud (in Norwegian only)
26) Telecom companies collaborate to stop SMS-related fraud (in Norwegian only)
27) The EBA's opinion on fraud mitigation
28) Participation in the regulatory sandbox to explore data sharing (in Norwegian only)
29) Security incidents are defined as intentional events, i.e., events where the purpose is to harm/attack. Operational incidents are defined as unintentional events caused by errors or deficiencies.
30) SWIFT's website: About us
31) CLS’ (Continuous Linked Settlement) website: A US financial institution that offers settlement services to its members in the foreign exchange market (FX).